What is Apache Directory Studio?
The Eclipse based LDAP browser and directory clientWhat is LDAP?
Apache Directory Studio is a complete directory tooling platform intended to be used with any LDAP server however it is particularly designed for use with ApacheDS. It is an Eclipse RCP application, composed of several Eclipse (OSGi) plugins, that can be easily upgraded with additional ones. These plugins can even run within Eclipse itself.
Source: http://directory.apache.org/studio/
The Lightweight Directory Access Protocol (LDAP) is an application protocol for reading and editing directories over an IP network. A directory is an organized set of records. For example, the telephone directory is an alphabetical list of persons and organizations, with each record having an address and phone number. A directory information tree often follows political, geographic, or organizational boundaries. LDAP directories often use Domain Name System (DNS) names for the highest levels. Deeper inside the directory might appear entries for people, departments, teams, printers, and documents.If this is your first time to LDAP, you might be wondering how is this different from an RDBMS. I suggest my readers to visit the following article Should I Use a Directory, a Database, or Both?
Source: http://en.wikipedia.org/wiki/LDAP
A Brief Background
We have a small startup company named Mojo Enterprises. We have four people, and two of them are admins. Our task is to create a hierarchical structure of our organization using LDAP because we anticipate the eventual growth of the company. We may have hundreds of people from different departments in five years time. Each has their own information and structure. These information and structure will be shared among different applications of the company. LDAP is a good protocol to meet all these requirements.
Layout the Structure
Let's define the important elements of the company.
Company Name: Mojo Enterprises
Members:
- Hugo Williams
- John Keats
- John Milton
- Robert Browning
- Hugo Williams
- John Keats
We need to assign the topmost parent of our structure. Logically, the name of the company fits that requirement. We'll pick the name mojo as the topmost parent.
Under the mojo we will assign our members. There are many ways to organize our members. We can organize them by gender, by job function, and etc. For this tutorial we'll organize them based on identity and roles. We'll put all the identities of each person in a separate element, while the roles will be placed on another element.
Under the roles we have two sub-divisions. Remember we have the regular users and the admins. What we'll do is divide the roles into elements.
Here's how our structure would like:
mojo
|
|--roles
| |
| |--admin
| |--regular
|
|--identities
|
|--guy1
|--guy2
|--guy3
|--guy4
We'll make the names a little bit formal, and make it conform with the naming convention of LDAP. For the topmost parent, we'll retain mojo. For roles, we'll use groups instead. For identities, we'll use usersWhen we're done with this tutorial, we should have the following structure:
It's really simple to do. All you need is an Apache Directory Studio, this tutorial, and patience.
Install the Apache Directory Studio
Before we can do any LDAP-related work, we need to have an IDE first. Although it's not required, we'll require it for this tutorial. And why not? It's free anyway.
To install the Apache Directory Studio, visit the following link http://directory.apache.org/studio/downloads.html Follow the instructions on that link
for the installation steps.
Create a New Server
Once you have installed the studio, we need to create a server. Here are the steps:
1. Open Apache Directory Studio.
3. Go to File, and click New. A popup window will open.
4. Expand the Apache DS folder, and select the Apache DS Server
5. Click Next.
6. Type-in any name for the server. For example, apache-ds-server
7. Click Finish.
8. A new server has been added on your Servers panel.
If you can't see the Servers panel, go the menu bar then click Window > Show View > Apache DS > Servers
9. Select your server, then click the Run button.
Your server should now be running.
Create a Connection
To browse the contents of the server, we need to create a connection. Here are the steps:
1. Right-click on your server.
2. Select LDAP Browser
3. Select Create a Connection. An alert message will popup indicating the a new connection has been created.
4. Go to the Connections panel.
If you can't see the Connections panel, go the menu bar then click Window > Show View > LDAP Browser > Connections
5. Double-click the name of the new connection you've created earlier.
6. The LDAP Browser panel should refresh and show the contents of the server.
Notice the topmost entry of this server is DIT, followed by the Root DSE.
7. Expand the Root DSE folder. There are two sub-entries: ou=schema and ou=system.
These are partitions in the server. Do not modify them unless you know what you're doing.
Create a New Partition
To add our company to the root tree, we need to create a new partition. Everything related to the company will be attached to this new partition. Here are the steps:
1. Go to the Servers panel, and right-click your server.
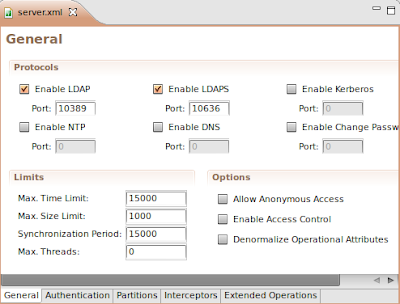
2. Select Open Configuration. A server.xml editor will appear on the main panel.
3. At the bottom part of server.xml, there are five tabs. Click the Partitions tab.
The Partitions tab should appear.
4. Click on Add and enter the following details for this new partition.
ID: mojo
Cache Size: 100
Suffix: o=mojo
5. Save your changes (CTRL + S). A new partition has been added.
6. Restart your Apache DS server.
7. Refresh the LDAP Browser panel.
8. Click on the Root DSE folder. A new editor will open containing the details of this folder.
Notice the namingContexts attribute. The namingContexts o=mojo shows in the lists. However it doesn't show under the Root DSE tree because we need to add the organization manually in the tree.
Add the Parent Organization
Our company is an organization. In LDAP, to represent a company we use the organization object which is represented by the alias o. So if our company's name is mojo, the Distinguished Name (dn) of the company is o=mojo. It's a naming convention. (The Distinguished Name is like the primary key or primary identity).
To create the organization object, follow the steps below:
1. Right-click on the Root DSE folder. Select New. Select New Context Entry
2. Select Create entry from scratch. Click Next. The Object classes window will appear.
3. Find the organization object. Select it then click Add
4. Click Next. Now you need to enter a Distinguished Name (dn). Click on the pulldown menu. Select o=mojo.
5. Click Next. The Attributes window will appear. Examine the values.
6. Click Finish. Notice the new partition now appears under the Root DSE.
Add the Organizational Units
Earlier we mentioned we'll structure our company based on users (contains personal information of the user) and groups (contains the authorization level of each person).
Both of these represent an organizational unit.
In LDAP, to represent an organizational unit we use the organizationalUnit object which is represented by the alias ou. So if we have a unit name users, the Distinguished Name (dn) is ou=users,o=mojo. Why is there an o=mojo? It's a naming convention. The same convention applies to groups. The Distinguished Name (dn) is ou=users,o=mojo. This can be likened the way we name URLS. For example, users.mojo.com or groups.mojo.com.
We'll add first the users unit. Here are the steps:
1. Go to the LDAP Browser panel. Expand the Root DSE folder.
2. Right-click the o=mojo entry. Select New. Select New Entry.
The Entry Creation Method window will appear.
3. Select Create entry from scratch. Click Next. The Object Classes window will appear.
4. Find the organizationalUnit object. Select it then click Add.
5. Click Next. Now you need to enter a Distinguished Name (dn).
The Parent field should read o=mojo.
On the RDN field enter ou. On the value field enter users. The DN Preview should read ou=users,o=mojo
6. Click Next. The Attributes window will appear. Examine the values.
7. Click Finish. We've just created the ou=users organizational unit.
Add the Second Organizational Units
We've just added the ou=users organizational unit. We need to add the organizational unit for groups as well. We'll follow the same steps.
1. Go to the LDAP Browser panel. Expand the Root DSE folder.
2. Right-click the o=mojo entry. Select New. Select New Entry.
The Entry Creation Method window will appear.
3. Select Create entry from scratch. Click Next. The Object Classes window will appear.
4. Find the organizationalUnit object. Select it then click Add.
5. Click Next. Now you need to enter a Distinguished Name (dn).
The Parent field should read o=mojo.
On the RDN field enter ou. On the value field enter groups. The DN Preview should read ou=groups,o=mojo
6. Click Next. The Attributes window will appear. Examine the values.
7. Click Finish. We've just created the ou=groups organizational unit.
Add the Staff
Now we need to add our four people:
- Hugo Williams
- John Keats
- John Milton
- Robert Browning
- Hugo Williams
- John Keats
Let's start with the ou=users. We'll be adding four persons. We'll represent each person using the inetOrgPerson object.
What's an inetOrgPerson object?
The inetOrgPerson object class is a general purpose object class thatAn inetOrgPerson can contain a user id (uid) and password (userPassword) which will be useful later for authenticating users from using LDAP.
holds attributes about people. The attributes it holds were chosen
to accommodate information requirements found in typical Internet and
Intranet directory service deployments.
Source: http://www.faqs.org/rfcs/rfc2798.html
Here are the steps we need to do:
1. Go to the LDAP Browser panel. Expand the Root DSE folder.
2. Expand the o=mojo entry.
3. Right-click the ou=users entry. Select New. Select New Entry.
The Entry Creation Method window will appear.
4. Select Create entry from scratch. Click Next. The Object Classes window will appear.
5. Find inetOrgPerson object. Select it then click Add.
6. Click Next. Now you need to enter a Distinguished Name (dn).
The Parent field should read ou=users,o=mojo.
On the RDN field enter cn. On the value field enter Hugo Williams.
The DN Preview should read cn=Hugo Williams,ou=users,o=mojo (cn represent Common Name).
7. Click Next. The Attributes window will appear. Examine the values.
8. Under the sn attribute, enter Williams (sn stands for Surname)
9. We need to add a username for this user. Right-click on the same window. Select New Attribute. The Attribute Type window will appear.
10. On the Attribute type field, enter uid. This will serve as the username of the person.
11. Click Next, then click Finish.
12. You're back on the Attributes window. On the uid attribute value, enter hwilliams
13. We need to add a password for this user. Right-click on the same window. Select New Attribute. The Attribute Type window will appear.
14. On the Attribute type field, enter userPassword. This will serve as the password of the person.
15. Click Next, then click Finish.
16. You will be asked to enter a password. Enter pass as the new password. Make sure that the Select Hash Method is set to Plaintext
17. Click OK.
A new entry has been added under the ou=users. The new entry is cn=Hugo Williams.
Now we need to add the remaining three users. In order to do that, just repeat the same steps earlier. Here are the details of the three remaining users.
Name: John Keats uid: jkeats userPassword: pass Name: John Milton uid: jmilton userPassword: pass Name: Robert Browning uid: rbrowning userPassword: passAdd the Authorization Levels
We have added the personal information, as well as the usernames and passwords, for each person under the ou=users. Now, we will be adding the authorization level for each of these persons.
We'll add them under ou=groups. We'll use the groupOfUniqueNames object to represent each role.
Let's add the User role first.
1. Go to the LDAP Browser panel. Expand the Root DSE folder.
2. Expand the o=mojo entry.
3. Right-click the ou=groups entry. Select New. Select New Entry.
The Entry Creation Method window will appear.
4. Select Create entry from scratch. Click Next. The Object Classes window will appear.
5. Find the groupOfUniqueNames object. Select it then click Add.
6. Click Next. Now you need to enter a Distinguished Name (dn).
The Parent field should read ou=groups,o=mojo.
On the RDN field enter cn. On the value field enter User
The DN Preview should read cn=User,ou=groups,o=mojo
8. Click Next. The Attributes window will appear. Examine the values.
Notice there's a uniqueMember attribute. We'll be placing the Distinguished Name (dn) of our users in this entry. One uniqueMember attribute will represents one user. This means we need to add three more uniqueMember attributes for a total of four uniqueMember attributes.
9. Right-click on the same window. Select New Attribute. The Attribute Type window will appear.
10. On the Attribute type field, enter uniqueMember.
11. Click Next, then click Finish.
12. We're back on the Attributes window. We need to add two more uniqueMembers (for a total of four uniqueMembers). Repeat the same steps for adding an attribute.
13. Now we need to fill-in the values for these attributes. In each entry add the dn of each user. Here are the Distinguished Name for each user.
cn=Hugo Williams,ou=users,o=mojo cn=John Keats,ou=users,o=mojo cn=John Milton,ou=users,o=mojo cn=Robert Browning,ou=users,o=mojo
14. Click Finish when you're done.
A new entry has been added under the ou=groups. The new entry is cn=User
Now we need another entry for the Admin role. We'll repeat the same steps.
1. Go to the LDAP Browser panel. Expand the Root DSE folder.
2. Expand the o=mojo entry.
3. Right-click the ou=groups entry. Select New. Select New Entry.
The Entry Creation Method window will appear.
4. Select Create entry from scratch. Click Next. The Object Classes window will appear.
5. Find the groupOfUniqueNames object. Select it then click Add.
6. Click Next. Now you need to enter a Distinguished Name (dn).
The Parent field should read ou=groups,o=mojo.
On the RDN field enter cn. On the value field enter Admin
The DN Preview should read cn=Admin,ou=groups,o=mojo
7. Click Next. The Attributes window will appear. Examine the values.
Notice there's a uniqueMember attribute. We'll be placing the Distinguished Name (dn) of our users in this entry. One uniqueMember attribute will represent one user. This means we need to add one more uniqueMember attributes for a total of two uniqueMember attributes.
8. Right-click on the same window. Select New Attribute. The Attribute Type window will appear.
9. On the Attribute type field, enter uniqueMember.
10. Click Next, then click Finish.
11. We're back on the Attributes window. We need to add one more uniqueMembers (for a total of two uniqueMembers). Repeat the same steps for adding an attribute.
12. Now we need to fill-in the values for these attributes. In each entry add the dn of each user. Here are the Distinguished Name for each user.
cn=Hugo Williams,ou=users,o=mojo cn=John Keats,ou=users,o=mojo
13. Click Finish when you're done.
A new entry has been added under the ou=groups. The new entry is cn=Admin
Here's the final structure:
Exporting the Data
If you need to backup your data or replicate the information in your LDAP, you can export the data. When the data is exported, it's saved in LDIF format. This format is actually a human-readable file. Here's the LDIF for this tutorial:
version: 1 dn: o=mojo objectClass: organization objectClass: extensibleObject objectClass: top o: mojo dn: ou=users,o=mojo objectClass: extensibleObject objectClass: organizationalUnit objectClass: top ou: users dn: ou=groups,o=mojo objectClass: extensibleObject objectClass: organizationalUnit objectClass: top ou: groups dn: cn=User,ou=groups,o=mojo objectClass: groupOfUniqueNames objectClass: top cn: User uniqueMember: cn=John Milton,ou=users,o=mojo uniqueMember: cn=Robert Browning,ou=users,o=mojo uniqueMember: cn=Hugo Williams,ou=users,o=mojo uniqueMember: cn=John Keats,ou=users,o=mojo dn: cn=Admin,ou=groups,o=mojo objectClass: groupOfUniqueNames objectClass: top cn: Admin uniqueMember: cn=Hugo Williams,ou=users,o=mojo uniqueMember: cn=John Keats,ou=users,o=mojo dn: cn=Robert Browning,ou=users,o=mojo objectClass: organizationalPerson objectClass: person objectClass: inetOrgPerson objectClass: top cn: Robert Browning sn: Browning uid: rbrowning userPassword:: cGFzcw== dn: cn=John Keats,ou=users,o=mojo objectClass: organizationalPerson objectClass: person objectClass: inetOrgPerson objectClass: top cn: John Keats sn: Keats uid: jkeats userPassword:: cGFzcw== dn: cn=Hugo Williams,ou=users,o=mojo objectClass: organizationalPerson objectClass: person objectClass: inetOrgPerson objectClass: top cn: Hugo Williams sn: Williams uid: hwilliams userPassword:: cGFzcw== dn: cn=John Milton,ou=users,o=mojo objectClass: organizationalPerson objectClass: person objectClass: inetOrgPerson objectClass: top cn: John Milton sn: Milton uid: jmilton userPassword:: cGFzcw==That's it. We've managed to setup our basic LDAP structure using Apache Directory Studio. We've also covered some of the popular LDAP objects.
|
Share the joy:
|

































Great tutorial, thank you very much
ReplyDeletevery useful
DeleteThanks alot very very useful.
DeleteHelped me very much, thanks!
ReplyDeleteVery helpful tutorial. Thanks for sharing.
ReplyDeleteIt helped me a lot..... thanks!!!
ReplyDeletevery helpful. thanks for your effort in writing this!
ReplyDeleteThis is a very well written article. Thank you for taking to time to contribute this!
ReplyDeleteMy only question here would be:
ReplyDeleteWhat is the password of the connection that was created?
Nevermind, found a good resource that has that information:
ReplyDeletehttp://directory.apache.org/studio/static/users_guide/ldap_browser/gettingstarted_create_connection.html
Just search for default bind password.
Thanks!
password: secret
ReplyDeleteGood way to start handling data from an LDAP repository with dummy values. Thanks!
ReplyDeletethis is da best LDAP tutorial ever !
ReplyDeletethx a lot that help me v v much.
Typo under Add the Organizational Units:
ReplyDeleteYou said:
The same convention applies to groups. The Distinguished Name (dn) is ou=users,o=mojo.
I think you meant:
The same convention applies to groups. The Distinguished Name (dn) is ou=groups,o=mojo.
great tutorial..............
ReplyDeleteafter creating different user can we authenticate user based on password and email id.......
I liked this tutorial - It opened my eyes.
ReplyDeleteI liked it so much that I went back to the top to add another organization, but when I did, I got an error. I can't add another organization?
Very much thankful to you, Nicely created start up
ReplyDelete-Ashish
Thanks, A Million
ReplyDeleteYou really help me.
Exactly what I needed !
ReplyDeleteThanks
Mozart Brocchini
Just wanted to say thank you for all the great tutorials. Your tutorials were the only ones (out of many I walked through) that actually helped me understand and successfully implement my own variation. Thanks!
ReplyDeleteReally good!Nice job
ReplyDeleteOne of the most simple and effective tutorial i have ever found on web for setting up Apache DS. Great job, keep it up. By the way, would it be possible to extend this tutorial or write up another tutorial to configure with tomcat server.
ReplyDeleteThanks
Devendran
Greate tutorial.nothing to say.Thanks a lot
ReplyDeleteThanks it is good material.
ReplyDeleteGreat Help for the LDAP learners,For me its more than great.Many thanks dear..
ReplyDeleteFantastic getting started tutorial, much appreciated
ReplyDeletewhat's after this ??
ReplyDeletehow to authenticate the user now ... i mean where we need to modify the code to authenticate the user on login screen ??
Same question. I can't log in with the users I've created through LDAP. I can only log in with ADMIN/ADMIN
Delete@Anonymous, have you checked the Tutorials section? This guide isn't meant to do any authentication. It's just for setting-up LDAP visually with Apache Directory Studio. Nothing more, nothing less. Try looking at the following guides:
ReplyDeletehttp://krams915.blogspot.com/2011/01/spring-security-mvc-using-ldap.html
http://krams915.blogspot.com/2011/01/spring-security-mvc-using-embedded-ldap.html
Thank you so much. This is the best tutorial that I had ever found on internet. Simple, Easy and Effective. Wonder of Thanks!!!!
ReplyDeleteFahad Sheikh
Thanks man! You saved my time. I was really struggling to add the organization at root level. That Partition thing did the trick for me. Your blog surpasses the apache documentation!
ReplyDeleteGood Work....
ReplyDeleteThanks alot, this helps me to understand in deeper the ldap.
ReplyDeleteGood job !
thank you this is helpful
ReplyDeleteNice tutorial, thanks. Was totally newbie to Directory service and LDAP, but now I can handle it.
ReplyDeleteI really appreciate you work, it is helped me a lot. Nice post.
ReplyDeleteExcelente Tutorial!!! Saludos desde Chile!!!
ReplyDeleteNice tutorial.
ReplyDeleteIf I want to modify the structure of the tree then is how to do this apacheDS?
Thank you very much man... really helpful
ReplyDeleteTHX!
ReplyDeleteGreat tutorial! like all the other ones!. Do you know something about to synchronize apacheDS with a user table in Oracle?
ReplyDeletean LDAP tutorial can't get better than this! Thanks a lot.
ReplyDeleteExcellent tutorial.. there are very few resources for LDAP beginners and this is the only one I was able to understand and follow. I have successfully used pGina on my Windows machines for testing, and I can authenticate to ApacheDS.. But the users are not added to any groups on the machines, so I really can't do anything.
ReplyDeleteIs there something I'm missing? or do I need to add anything to my configuration to tell Windows what Group each user should be a member of ?
Thanks !
Thanks a lot...!!!!! made my work less cumbersome... :)
ReplyDeleteHi Krams,
ReplyDeleteWhen i am restarting the apache -ds-server then it is not starting again please give a suggestion and please send the complete example with jar files.
i have read your blogs and follow your blogs but when i stop the apche-ds-server and again starts the server then it is not start.
And when i an trying to add manually "Root DSE tree because we need to add the organization manually in the tree" then error is coming on on LDAP Browser.
"#!RESULT ERROR
#!CONNECTION ldap://localhost:10389
#!DATE 2012-06-17T18:19:01.332
#!ERROR [LDAP: error code 50 - INSUFFICIENT_ACCESS_RIGHTS: failed for Modify Request Object : '' Modification[0] Operation : delete Modification namingContexts: ou=schema Modification[1] Operation : add Modification namingContexts: ou=mojo : ERR_17 The rootDSE cannot be modified!]
dn:
changetype: modify
delete: namingContexts
namingContexts: ou=schema
-
add: namingContexts
namingContexts: ou=mojo
-
"
great!
ReplyDeleteFantastic tutorial - thanks kindly. A suggestion for a follow-up: Setting up access controls in ApacheDS
ReplyDeleteextending on the comment above, specifically, how do you add access controls to allow users to change only their own password, and allow admin group members to change anything?
ReplyDeleteIt saved my life!!!
ReplyDeleteI needed to get a quick LDAP directory up and running in order to test some Grails code. The Apache documentation seemed to be leaving out some key points, so I did another search and found this. Easy and complete! Thanks for your excellent work.
ReplyDeleteAfter playing with this stuff for two days, it's nice to see a tutorial written in plain English! Thank you!
ReplyDeleteThis is my first time working with LDAP. I found this tutorial very helpful to understand core of LDAP. Thanks!!
ReplyDeleteVery helpful my first time also!! Thank you a lot!!
ReplyDeleteThanks!!
ReplyDeleteThanks a lot for shared a good article in the serious world !!
ReplyDeleteThank you very much. It is very helpful.
ReplyDeleteThanks a bunch. Great article!
ReplyDeleteThanks a lot.... Helped me a lot.
ReplyDeleteExcellent tutorial, Thanks!
ReplyDeleteJust an FYI - the instructions here do not seem to work correctly with ApacheDS 2.0. For some reason the default configuration of ApacheDS has changed such that it is not possible to add an organization at the top level. Apache Directory Studio will report a error when attempting to add an objectClass of organization to the root DSE.
ReplyDeleteExcellent Tutorial Very Neatly explained
ReplyDeleteMuy buen tutorial muchas gracias!!!
ReplyDeletefrom Uruguay :D
Hi,
ReplyDeleteI have 2 queries. Please can help or direct me regarding these: We are currently using WSO2 4.0 M8. We created some users and were using Apache Studio to view the Apache DS schema embedded in the WSO2 identity server
We were able to see the user details, claims, uid etc. But, we are not able to see the gid (POSIX GID - Group id).
And we were not able to add it as a new attribute as it is not displayed in the attribute Type list (drop down box). But the Schema Browser tab shows gidNumber attribute type in it.
We want to view the GiDs of the users. Please do tell us a way to add gid as a new attribute so I can view the user’s Gid.
2. Furthermore I also want to add PAM as an "ou" and use PAM for authentication and Mapping LDAP users to Linux user groups how can I go about this.
Thanks in advance.
Well done. Thanks.
ReplyDeleteVery good tutorial.. I like to thank the contributor for sharing his knowledge..
ReplyDeletepls help me to add new user to apache DS through java code
ReplyDeleteVery well presented.
ReplyDeleteThis articles help a lot!! Tx a million!!
ReplyDeleteSimplest of all. Did it even if I donno anything of ldap...
ReplyDeleteThank you.
This post was really helpful. Thanks
ReplyDeleteThis tutorial was helpful...
ReplyDeleteThanks a lot
Bits
Really nice tutorial man... thank you!! You made me avoid to read extense official documentation :D
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteNice tutorial! Thank you!
ReplyDeleteThanks you for the tutorial. It was really helpful and informative
ReplyDeleteMan you are Rock! . I am using Apache client API in Java to connect to DS for my Security system Authentication system. It uses Active Directory and Apache DS. This way I can create/modify/edit Users, GROUPs and OUs, easily form my front end in human readable format. I have to emulate this steps in Java using API. Thank you so much for putting this simple tutorial.
ReplyDeleteI'M NOT ABLE TO CREATE A SERVER ,THAT OPTION IS NOT AVAILABLE IN MY APACHE DIRECTORY STUDIO.WHAT SHOULD I DO?
ReplyDeleteHi Krams,
ReplyDeleteI'm also facing the same problem as no apacheds server option available in apache directory studio v2.0
Nice tutorial! Thank you!
ReplyDeleteThank you sir !! Very well explained !
ReplyDeleteThanks Krams,
ReplyDeleteIt Really helped me .
Thanks for tutorial krams
ReplyDeleteGreat Stuff. Thanks a lot
ReplyDeleteNice tutorial for starters to get familiar with LDAP. Thanks Dude.
ReplyDeleteVery helpful, thank you
ReplyDeleteHi... Thanks for this great tutorial. Now i have setup LDAP server in my machine. If want to search these directory items, how to do? I am not able to search the content from some other PC!!!
ReplyDeleteI simply could not go away your website prior to suggesting that I really enjoyed the usual info an individual
ReplyDeleteprovide to your guests? Is going to be back often to check up on
new posts
Visit my web-site - Abercrombie Pas Cher
Congratulations for a really well done job.
ReplyDeleteThank you.
very nice tutorial..really helpful for beginners
ReplyDeleteTruly an awesome and amazing tutorial. Was super confused until I saw this tutorial. Thank you!
ReplyDeleteHi,I'm new to LDAP and I need to create a structure which involves the relations of the database. I want to have a key associated with each attribute of the relation.In this case,which ContextEntry should I be using to specify the (attribute,key) pair.Thank you!!
ReplyDeleteSimple and clear explanation, Thanks for your tutorial.
ReplyDeleteExcellent tutorial for the beginners. helped me a lot to understand the core definitions thanks :)
ReplyDeleteVery good tutorial, helped me a lot !Thanks man.
ReplyDeletecant we create "o=mojo" directly using java. not with UI.
ReplyDeletethis is really helpful
ReplyDeleteCan some one tell me that how can i add user's access permissions in ApacheDS 2.0.0 through java code..
ReplyDeleteif someone want to start with ldap.start from here
ReplyDeletegreat tutorial .It helped me to understand the basic stuff about LDAP
ReplyDeletethank you,
ReplyDeleteGreat Tutorial ... Thanks a Lot.. :-)
ReplyDeleteWell done! Thank you.
ReplyDeletethank you so much! save my ass!
ReplyDeleteNice tutorial.
ReplyDeleteIts such an amazing tutorial. I replicated whatever you have taught.Thanks a lot. This tutorial had been quiet helpful
ReplyDeleteIntroduction
ReplyDeletehttp://www.21cssindia.com/courses/ldap-online-training-103.html
LDAP - Overview
A brief History of LDAP - LDAP Overview - LDAP vs. Database - LDAP Usage Summary
LDAP Data (Object) Model - Object Tree Structure - Attributes - Object Classes
Employees to learn at their own pace and maintain control of learning “where, when and how” with boundless access 24/7by 21st Century Software Solutions. contact@21cssindia.com ---- Call Us +919000444287
In step 4, I don't see 'Apache DS Server' as an option. Only Apache DS 2.0 Configuration File and Apache DS Configuration FIle. How to create a server?
ReplyDeleteI had the same issue, here is how I did it:
DeleteThere is a "Servers" panel on the bottom left corner of your screen, next to the "Connections" panel. You can create an LDAP server by clicking on the "New server" button.
I had the same problem, and this solution solved it.
Delete-Thanks
hey how do you include email addresses for the users?
ReplyDeleteHi , You can add "mail" attribute the users
DeleteHi,
ReplyDeleteWhat version of apacheDS did you used on this tutorial?
What's the difference of using 2.0 M17?
Thanks,
R
This is very useful article.Thanks for sharing.I tried this and it is working well.
ReplyDeleteI have two queries ..
1)What is the difference between "GroupOfUniqueNames" and "GroupOfNames"?I chose "groupOfNames" .Will there be an impact?
2)In this article,you have explained how to create groups and add members to it.Could you also let us know how to give authorisation level to groups?Such as ReadGroup should be only able to Read and RWGroup should be able to Read and Write.
This is really awesome.... not even a single question raised while following the steps.. some pictures are missing ( not a big problem though ) ...
ReplyDeleteLDAP Online Training, ONLINE TRAINING – IT SUPPORT – CORPORATE TRAINING http://www.21cssindia.com/courses/ldap-online-training-103.html The 21st Century Software Solutions of India offers one of the Largest conglomerations of Software Training, IT Support, Corporate Training institute in India - +919000444287 - +917386622889 - Visakhapatnam,Hyderabad LDAP Online Training, LDAP Training, LDAP, LDAP Online Training| LDAP Training| LDAP| "Courses at 21st Century Software Solutions
ReplyDeleteTalend Online Training -Hyperion Online Training - IBM Unica Online Training - Siteminder Online Training - SharePoint Online Training - Informatica Online Training - SalesForce Online Training - Many more… | Call Us +917386622889 - +919000444287 - contact@21cssindia.com
Visit: http://www.21cssindia.com/courses.html"
Well structured. Many thanks.
ReplyDeleteNice Article,very helpful - Many Thanks
ReplyDeleteThanks Lot , Great work
ReplyDeletethank you so much, excellent
ReplyDeleteVery good tutorial, thanks a lot.
ReplyDeleteThanks for this excellent tutorial. Very good job.
ReplyDeleteThank you very well written article . But I am not able to go beyond Add the Authorization Levels as the error I get is " the connection is read only " Where to change the settings?
ReplyDeletethanks for such a nice article.
ReplyDeleteI have a question to ask:
Can we add specific time or inactive for users?
Thank you very much. you saved my time.
ReplyDeletelove it keep up the good work mlg
ReplyDeleteThank you very much!!!
ReplyDeleteAny way to lock or disable user account.
ReplyDeleteAwesome tutuorial.. Very Helpful in setting up a localhost LDAP server
ReplyDeletecan some please explain the steps to create groups with posixGroup object class...
ReplyDeletethanks for your help....
ReplyDeletethanks for positing.
ReplyDeleteGood piece of information and put up together very nicely.
ReplyDeleteThanks
This is fabulous. For the newest version (2.0.0) there were some minor changes. I've added those to my blog.
ReplyDeletehttp://xinerama.blogspot.kr/2015/11/rhcsa.html
Thanks for the post. It really helped me i spent lot of time in getting this kind of information on internet
ReplyDeleteThanks For your help. Can anybody help me to understand Enable/Disable user account in ApacheDS?
ReplyDeleteThank you for your effort. This is wonderful..
ReplyDeleteGreat article
ReplyDeleteit's informative and very good article. I have searched many google pages and tired. This article is simply superb. Thank you.
ReplyDeleteThis was a really wonderful post. Thank you for your detailed information it is such a great help for my business. Find Local Business Directory
ReplyDeleteI tried to create ldif structure manually years back, it was very complex. This blog is superb, thanks for the detailed explanation.
ReplyDeleteHi,
ReplyDeleteIs there any way to sync with Active Directory? I don´t mean a connections to query, list or modify objects in AD.
What I really need is sync with AD (have the AD Database in ApacheDS) and also have a configuration that let´s synchronization happens went there is a change in AD.
Thanks in advance
Best tutorial of Ldap ever!!
ReplyDeleteThanks alots for clear understand..
ReplyDeleteWe have a small startup company named Mojo Enterprises. We have four people, and two of them are admins. Our task is to create a hierarchical structure of our organization using LDAP because we anticipate the eventual growth of the company.
ReplyDeleteOxford Security
ADS Ldap Configuration at its best..
ReplyDeleteVery informative error.Thank you author for posting this kind of errors .
ReplyDeletehttp://www.wikitechy.com/fix-error/not-able-to-access-oracle-database-on-other-computer
Both are really good.
Cheers,
Venkat
Even 5 years later it's still very helpful, thank you for the post!
ReplyDeleteI agree with @protoswype. Thanks a lot!!!!! This is the best simple article I've found on inet!!
ReplyDeleteI have read your blog its very attractive and impressive. I like it your blog.
ReplyDeleteSpring online training Spring online training Spring Hibernate online training Spring Hibernate online training Java online training
spring training in chennai spring hibernate training in chennai
Great job ! It has made my day.
ReplyDeleteشركة تسليك مجاري المطبخ بالرياض
ReplyDeleteشركة تسليك مجاري بالرياض
شركة تسليك مجارى الحمام بالرياض
level تسليك المجاري بالرياض
افضل شركة تنظيف بالرياض
تنظيف شقق بالرياض
شركة تنظيف منازل بالرياض
شركة غسيل خزنات بالرياض
افضل شركة مكافحة حشرات بالرياض
رش مبيدات بالرياض
شركة تخزين عفش بالرياض
شركة تنظيف مجالس بالرياض
تنظيف فلل بالرياض
ابى شركة تنظيف بالرياض
Good Job! Great article
ReplyDeleteits very nice blog its very best information if you looking for How to Get Rid of Trovi, Delete Trovi Virus or uninstall Trovi completely visit now How to Remove Trovi, How to Get Rid of Trovi from Firefox, Chrome, Computer, Windows, Mac
ReplyDeleteExcellent Article if you are looking for uninstall ask toolbar, remove ask toolbar delete ask toolbar or get rid of ask toolbar from Firefox, chrome or internet explorer then come to the website How to Get Rid of Ask Toolbar, Remove Ask Toolbar from Firefox, Google Chrome, Internet Explorer, Mac, Windows, Computer
ReplyDeletehi,this is awesome but i faced problem when create new entry using createSubcontext took 1 sec approx for one request but suppose 1000 request simultaneous hit than it takes more time.
ReplyDeleteDo you have any solution or approach to process all 1000 request in few seconds
Free easy & simple way to learn java online and much more.. go to =>> http://foundjava.blogspot.in
ReplyDeleteHi,
ReplyDeleteI have followed this step create a ldap server but I am unable to connect to this server can anyone help me how to make connection to the server.
ReplyDeletenice article great post comment information thanks for sharing.
gclub casino
gclub
gclub casino
I have seen a lot of blogs and Info. on other Blogs and Web sites But in this Hadoop Blog Information is useful very thanks for sharing it........
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteEduwizz online training is one of the Best Online Training Institute in Hyderabad, Bangalore. Eduwizz provide courses Hybris , Guidewire, Adobe, RPA , Machine Learning, AWS, Statistics for Beginners, Commvault Training, Devops, Netapps, TSM, EMC, Data Science, Internet of Things , IBM Blue-Mix , Hybris ,Angular JS , Node JS , Express JS , Business Analyst, Selenium testing with webdriver.
ReplyDeleteThis is a good article that explains it very well. Although for some reason I cannot connect from Thunderbird using an LDAP directory using the user credentials
ReplyDeleteThis is an excellent blog, thanks for sharing UI Online Course
ReplyDeleteGreat and Interesting article... Thanks for sharing your information about blog....
ReplyDeleteJava Training in Chennai
Excellent article.,nice explanation ...
ReplyDeleteBest Java Training in Chennai
Thanks for sharing...
ReplyDeletequickbooks intuit number
quickbooks intuit support number
intuit quickbooks number
quickbooks intuit software
quickbooks payroll service
quickbooks payroll service number
quickbooks payroll support number
quickbooks payroll support phone number
quickbooks bookkeeping services
virtual bookkeeping services
remote bookkeeping serivices
Professional bookkeeping serviecs
Hi Nice Information.One Can also Check out professional Services
ReplyDeleteMicrosoft CRM Training Online
Hadoop Admin Training Course
Thanks for sharing...
ReplyDeleteQuickbooks intuit software
Nice to read this article... Thanks for sharing.....
ReplyDeleteAndroid Course
Hello guys!
ReplyDeleteWhat can you tell me about this locksmiths device? http://24locksmithjerseycity.com/ I'm looking for hight reliable locksmiths for my car doors in Locksmith Jersey City.
Thanks on Salesforce online training is a good sharing
ReplyDeleteSalesForce Online Training
Your Post is Useful
ReplyDeleteClick Here To Latest Recruitment : JPC Hospital Recruitment 2017.
Successit is one of the best SAP Online/Classrooms training institute in Hyderabad.We Provide SAP courses for SAP MM,SAP-WM,SAP-SRM,SAP-PP ,SAP-EWM ,SAP-SD,SAP-APO ,SAP-FI/CO ,SAP-S/4 HANA,SAP-GTS ,SAP-TM,SAP-BW/BI,SAP-BO,SAP-ABAP/CA ,SAP-HR,SAP-PM,SAP-PS...etc.at affordable prices.
ReplyDelete
ReplyDeleteThanks for sharing this good blog.
Core Java Online Training
This design is wicked! You most certainly know how to keep a reader entertained. Between your wit and your videos, I was almost moved to start my own blog (well, almost...HaHa!) Fantastic job. I really enjoyed what you had to say, and more than that, how you presented it. Too cool!it support melbourne
ReplyDeleteThanks for posting the useful information to my vision. This is excellent information,.
ReplyDeletecorporate training services in hyd
Australia Best Tutor is one of the best Online Assignment Help providers at an affordable price. Here All Learners or Students are getting best quality assignment help with reference and styles formatting.
ReplyDeleteVisit us for more Information
Australia Best Tutor
Sydney, NSW, Australia
Call @ +61-730-407-305
Live Chat @ https://www.australiabesttutor.com
Our Services
Online assignment help
my assignment help Student
Assignment help Student
help with assignment Student
Students instant assignment help
Finding the time and actual effort to create a superb article like this is great thing. I’ll learn many new stuff right here! Good luck for the next post buddy..
ReplyDeleteBest Industrial Training in Noida
Best Industrial Training in Noida
It is really a great work and the way in which u r sharing the knowledge is excellent.
ReplyDeleteThanks for helping me to understand basic concepts.
Also Check out the : https://www.credosystemz.com/training-in-chennai/best-data-science-training-in-chennai/
Hadoop is more demand nowadays and more jobs are awaiting for people with Hadoop skills. There are good training institutes with experienced trainers for Hadoop training in Hyderabad. Join now.
ReplyDeleteJust now you decided to be one of the demand in Hadoop training in Hyderabad. Yes you can be an desirable resource for your company because you are just on the verge of learning Hadoop technology.There are number of professionals trained in Hadoop. So it’s easy to grab a job with big companies.
ReplyDeleteThank you very much for the information, it has been very useful to me to configure my hosting.
ReplyDeleteNeeded to compose you a very little word to thank you yet again regarding the nice suggestions you’ve contributed here.
ReplyDeletebest wireless bluetooth headphones
best power bank for mobile
dual sim smartphone
keypad mobiles with wifi and whatsapp
best smartphone accessories
basic mobile phones dual sim low price
Best Mouse under 300
best wired Mouse under 500
full hd computer monitor
nice post..
ReplyDeleteeducation franchise opportunities
The Singapore 4D Result can help you to get to the perfect betting destination. The latest results can help you learn whether you've come to be any richer. Therefore, if you're looking for The Singapore pools 4d results today like The toto Result Singapore , The 4d result Singapore or The Magnum 4D Result
ReplyDelete. If you're looking for The Singapore 4D Result today , magnum website is where to find the results. All you have to do is to learn to minimize your possible loss instead of going crazy by pursuing the different strategies on how best to maximize your own profits by the money that you've been in a position to spend on the The Singapore 4d. Then you watch for the outcomes of them to decide if you've won or not. Therefore, if you're looking for Magnum 4D past result or The toto 4D Results history to understand which numbers were won lottery in past and the number of times then you need to have a look at a website that's active and have fresh database of The 4D Past Result and the update their site continuously.
In any sort of gambling, the longer you remain in the game the greater your odds of losing. It's possible to elect for The 4d results small in addition to big game. Now the Toto 4D lottery game is extremely common in nearly all sections of the country. Exploring the The 4D live Results Singapore pools information is able to help you identify what you've won and what you might have lost. It's quite tough to find reliable info about the biggest prize that's been handed out in the history of The Singapore Pools 4D Result
This blog is the general information for the feature. You got a good work for these blog.We have a developing our creative content of this mind.Thank you for this blog. This for very interesting and useful.
ReplyDeleteHadoop Training in Chennai
Hadoop Training in Bangalore
Big data training in tambaram
Big data training in Sholinganallur
Big data training in annanagar
Thanks for sharing this blog. This very important and informative blog Learned a lot of new things from your post! Good creation and HATS OFF to the creativity of your mind.
ReplyDeleteVery interesting and useful blog!
simultaneous interpretation booth
silent disco headphones
silent disco headphones
silent disco headphones
simultaneous interpretation equipment
simultaneous interpretation equipment
bosch simultaneous interpretation system
Amazing Post. The article is very much informative. Do update more.
ReplyDeleteSalesforce Training in Chennai
Salesforce Training
Salesforce Training Institute in Chennai
Salesforce Course in Chennai
The knowledge of technology you have been sharing thorough this post is very much helpful to develop new idea. here by i also want to share this.
ReplyDeleteDevops Training in pune
Devops training in tambaram
Devops training in velachery
Devops training in annanagar
DevOps online Training
All the points you described so beautiful. Every time i read your i blog and i am so surprised that how you can write so well.
ReplyDeletepython training in rajajinagar
Python training in btm
Python training in usa
Nice blog..! I really loved reading through this article. Thanks for sharing such a amazing post with us and keep blogging...
ReplyDeleteABiNitio online training in Hyderabad
ABiNitio training in Hyderabad
online ABiNitio training in Hyderabad
Nice tutorial. Thanks for sharing the valuable information. it’s really helpful. Who want to learn this blog most helpful. Keep sharing on updated tutorials…
ReplyDeletejava training in chennai | java training in bangalore
java online training | java training in pune
ReplyDeletesuch a wonderful article...very interesting to read ....thanks for sharining .............
Hadoop online training in pune
Hadoop training in mumbai
Bigdata Hadoop training in usa
interesting blog, here lot of valuable information is available, it is very useful information. we offers this Big Data online training at low caste and with real time trainers. please visit our site for more details Big Data training
ReplyDeleteThis is a good post. This post give truly quality information. I’m definitely going to look into it. Really very useful tips are provided here. thank you so much. Keep up the good works.
ReplyDeleteData Science course in kalyan nagar | Data Science course in OMR
Data Science course in chennai | Data science course in velachery
Data science course in jaya nagar
BEST Online SAS TRAINING
ReplyDeleteVery nice tutorial. This blog is very useful and informative for every one thanks for sharing.
ReplyDeleteDevOps Training in Hyderabad
Thanks for the Nice Blog i really appreciate it
ReplyDeleteSEO Training
Thanks for sharing this blog very informative and useful content.
ReplyDeletepega online Training